Hello NullByte!
This will be my first How To series.
In this tutorial you'll learn what SQL is, what SQL injection is and how it benefits you as a hacker.
I strongly recommend learning at least the basics of PHP before attempting to learn/use SQL Injection.
list of references;
SQL Wikipedia
DVWA Learn by trying!
PHP
Table of Contents:
1- What are Databases?
2- What is SQL and how does it work?
- 2.1. Defining SQL.
- 2.2. Explaining SQL's usage and Syntax.
- 2.3. SQL's integration in other programming languages.
- 2.4. Conclusion.
3- What is SQL Injection?
- 3.1 Defining SQL Injection.
- 3.2 How does SQLi work?
4- Final Conclusion.
So, let's begin shall we?
1. What Are Databases?
So what is a Database? Simply put, it's the place where all your data is stored, therefore "Data-Base".
Databases are basically a structure of tables, each table containing a set of Rows defining the data and columns containing the data.
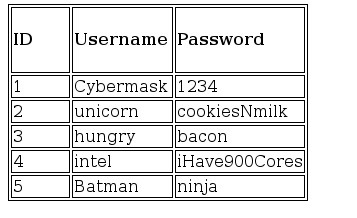
Let's take this as an example.
Be this our table, called "UserData".
It contains 3 Rows of data, first being the "ID", second being the "Username" and third being the "Password".
This way, we have some data stored for our users.
So, let's break it down!
Each column here contains a bunch of data specific to one entity (In this case, a user.)
For example, the first column in this table contains data that belongs to the user "CyberMask", the second to the user "unicorn".
So if I wanted to know CyberMask's password, I'd look for the Row "Password" corresponding the the column where the user is "CyberMask". You could think of it as an an X-axis Y-axis kinda thing.
So that's a database, but what does SQL have to do with this?
2. What Is SQL and How Does It Work?
So what does all that hallahulla has to do with SQL?!
This section will contain the following:
- Defining SQL.
- Explaining SQL's usage and Syntax.
- SQL's integration in other programming languages.
- Conclusion.
- Defining SQL:
SQL is short for Structered-Query-Language, or Sequel as some like to call it.
It is a language commonly used for database management.
In short, SQL tells databases what to do.
Let's say I have a million users in my database and I wanted to get the ID of a specific user, now searching manually would be insane wouldn't it?
This is where SQL comes in, I want to tell the database to select the ID of CyberMask and print it out, so how does that work?
- Explaining SQL's usage and Syntax:
Let's take a code snippet as our example:

Does it make sense already?
This is called a Query; Queries are simply pieces of code you run.
They're different from other languages where each query runs separatly and independently as instructions given to the database through the database engine.
So let's break it down!
SELECT tells the database to select one or multiple values.
ID is the value SELECT is going to select.
FROM tells the database what table to use, in this case it's UserData.
WHERE here is a condition, simply put, it's telling the database to only select ID where certainValue=something. In our case, we want the password from the column where the Username Row has the value CyberMask. Makes sense?
So now that we've covered SQL's basic usage to retrieve data, let's go further down and explain how websites use it!
- SQL's integration in other programming languages:
So now we know how to fetch data from the database. But how does that relate to websites hacking and other cyber entities?
The answer is simple, SQL can be integrated in other languages such as PHP and C# for example.
let's take PHP as an example. (PHP is a server-side programming language for web applications)

You see how the syntax is very similiar?
It's pretty simple how SQL is integrated in other languages, as for the most part the Query's syntax is almost always the same!
So what does that exactly mean? It means that any website that uses a database is most likely using SQL aswell as it's a key ingredient in the database management world.
- Conclusion:
SQL is a powerful language in it's own unique ways. Despite it's simplicity, it's used on a VERY large scale.
It can be used on it's own, aswell as integrated into other programming languages.
It behaves differently compared to most programming languages, as it runs individually as a set of instructions to the database.
Now, we know what SQL is. How does that relate to hacking?
Well, let's find out!
3. What Is SQL Injection?
- Defining SQL Injection:
SQL Injection is actually just what the name suggests, to inject SQL.
No really, it's as simple as that.
What you do is inject malicious code in an already existing Query, that way you can manipulate the set of instructions before it's run through the database.
SQL Injection at it's best can solely give you full control of the operating system that runs the database. Imagine that.
So how does that work?
- How does SQLi work?
We'll only talk theory here for now.
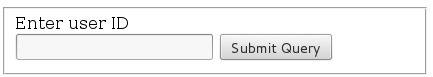
Let's take this form as our example:
Form runs this query:
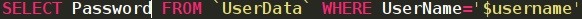
So let's break this down.
In the php code I assigned a variable called "$username" to that textbox, so anything I type in the textbox will be put in the place of $username inside the query.
As a rule of thumb, $username = whatever I type into that textbox.
So in theory, if I type a query in that textbox, it should get run.
Therefore the "injection" concept.
Ofcourse, I would need to type a bit more than a SELECT query, but that's yet to come!
4. Final Conclusion:
SQL (short for Sequel) is the most used database management language.
It's a simple language in the form of instructions called Queries, each instruction (Query) being run individually in real-time through the database.
SQL Can be integrated in other programming languages.
SQL Injection is the act of squeezing malicious code inside an existing Query.
SQL Injection is used in order to gather data/run malicious code on the operating system.
It can be a great addition to your skillset as a hacker.
That would be all!
I hope this becomes a useful contribution to the community!
Furthermore, kindly point out anything you would like to see changed/improved/added to this tutorial.
Cheers~
CM.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















7 Comments
Many thanks; wifi hacking and SQL injection are the two areas I need to focus on. Much appreciated.
Great. You can add a reference of DVWA for testing purposes.
Thank you very much! I just started studying for a Database cert and this helps tremendously.
In the beginning of part 4:
"SQL (short for Sequel) is the most used database management language."
SQL does not stand for sequel. SQL stands for 'Structured Query Language'
https://en.wikipedia.org/wiki/SQL
Microsoft however does like to pronounce it 'Sequel' whilst others say S-Q-L.
And if i was you, I'd also add the most basic advice to protect from SQL injection: use variables to hold your data. parse anything entered into that field into @thisVariable, then when running the query, you'll run it against the @thisVariable Parameter.
Thanks for the insight, I'll fix it right away.
As for the protection, I'll include it in some of the next tutorials, it's planned out.
In 2 he defines SQL as 'Structured Query Language', I believe when he said SQL is short for Sequel he didn't mean it that's what it stands for. I assume he mean, "this is just another way of saying it."
Glad I could help!
Share Your Thoughts